Search Knowledge Base
KB #240119: Encrypted Databases Not Accessible After Reboot but are Accessible After Manually Restarting SQL Server
Type:
Workaround
Summary:
Encrypted databases may be inaccessible after reboot (listed as Suspect or Recovery Pending). If the Master Database is encrypted, SQL Server will not even start at reboot. However, if you manually start/restart SQL Server later, encrypted databases become accessible. This is due to Windows starting the SQL Server Service before the Encryptionizer Key Management Service (KMS) has fully started. This particularly affects Windows 10 and Server 2016 or later, due to Windows Defender slowing down the KMS startup time.
Additional Information:
Several workarounds are shown below:
- Set the SQL Server Service (and any dependent Services) to Delayed Auto-Start
- Make the SQL Server Service dependent on the KMS Service
- Add a KMS Process Exclusion to Windows Defender
- (See notes at the bottom if you are using the script-based Distribution Installer)
- Enter a Command Window As Administrator.
- Run the following command:
sc config servicekey start= delayed-auto. For example:
sc config mssqlserver start= delayed-auto - As in the Services tab example, repeat for any services that are dependent on the SQL Server Service, for example:
sc config SQLSERVERAGENT start= delayed-auto - Start a Command Window As Administrator.
- Run this command line specifying the full path to the REG file you created
REG IMPORT c:\temp\exclusion.reg
1) Set the SQL Server Service to Delayed Auto-Start
(Not suitable for Clustered instances) This will instruct Windows to delay starting the Service(s) for approximately one minute after reboot. During this time, KMS will be able to fully start before the SQL Server Service starts. You can use the Services Tab or Command Line. You can apply this by the Services Tab or by Command Line.
To apply solution by the Services Tab
Start the Services tab (or Run Services.msc). Select the SQL Server Service. Change the Service Start type from Automatic to Automatic (Delayed Start).
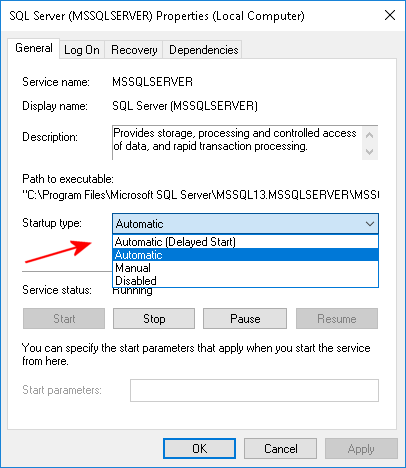
Note that you must also set Delayed Auto Start for any Auto Start services that depend on the SQL Server Service. For example, the associated SQL Server Agent Service and the SQL Server Launchpad (SQL Server 2016).
In order to see the Service(s) that are dependent on the SQL Server Service, click the
Dependencies tab. You will see the dependent services, if any, in the lower pane. For example:
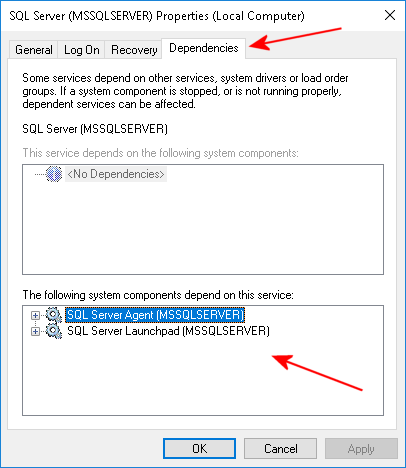
Both of these Services (if Auto Start) must also be set to Delayed Auto Start.
To apply solution by Command Line
Delayed Auto Start waits approximately two minutes after reboot before starting a service. If startup time is critical, use technique #2 or #3.
2) Make the SQL Server Service dependent on the KMS Service
(Recommended for Clustered instances. Apply to both nodes.) Make the SQL Server Service dependent on the Encryptionizer Key Management Service (Service Registry Key: NLCBTASK). Use this technique (or #3) if startup time is critical. You can use RegEdit or the following Command Line (in a Command Window as Administrator):
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\serviceName /v DependOnService /t REG_MULTI_SZ /d "NLCBTASK"
Where serviceName is the Registry Key of the SQL Server service, for example:
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\MSSQLSERVER /v DependOnService /t REG_MULTI_SZ /d "NLCBTASK"
3) Add a KMS Process Exclusion to Windows Defender
Add a Process Exclusion to Windows Defender for the Encryptionizer Key Management Service (KMS) Executable. Use this technique (or #2) if startup time is critical.
Locate the service executable (NLCBTASK.EXE) in the Encryptionizer installation directory, typically:
C:\Program Files (x86)\NetLib\SECSQL\NLCBTASK.EXE
You can add the exclusion from Control Panel->Windows Defender->Settings->Exclusions->Add Exclusions>Processes.
Alternatively use Notepad to create a text file, for example, c:\temp\exclusion.reg. Add the following text to the file, specifying the full path to the NLCBTASK.EXE executable. For example:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Processes] "c:\\Program Files (x86)\\NetLib\\SECSQL\\nlcbtask.exe"=dword:00000000
Note the double backslashes \\ in the path. This is required to properly import into the Registry. Then import the REG file using RegEdit, or import from a command line with this procedure:
4) Lastly, if you are using the Encryptionizer Script Based Distribution Installer
You can specify Delayed Start or Dependency for the SQL Server Service in the INI file by using the delay= or depend= Value. For example:
;install.ini [install] dir=%programfiles%\netlib\secsql reg=@reg.txt reboot=yes secure=secure.xml [mssqlserver] api=true ; set SQL service and any dependent services to delayed start delay=true ; alternatively, make SQL Server service dependent on the KMS Service depend=true
Last modified: 4/16/2025
