Legacy Systems: Encryption for Aging Databases
Despite their outdated nature, legacy systems continue to play a critical role in many organizations’ day-to-day operations. These systems are often written in antiquated programming languages and may rely on unsupported third-party utilities, making them difficult and expensive to upgrade or replace. Furthermore, the obsolete security features in legacy systems make them vulnerable to attacks, which can have serious consequences for organizations.
Modern regulations and company policies demand that all systems and their data be secure, with encryption as a crucial tool for protecting sensitive information. Despite their continued usefulness, organizations must address the risks associated with legacy systems, including the need to secure their data with encryption.
Importance of Encryption For Legacy Applications
Legacy systems continue to process and store sensitive information, making encryption a fundamental tool for protecting data privacy, and preventing unauthorized access. Encryption involves encoding plain text or data using a mathematical algorithm, which can only be deciphered by authorized parties with access to a decryption key. Here are some of the principal reasons why encryption is important:
- Protecting data privacy:
Encryption ensures that sensitive data remains confidential, even if it falls into the wrong hands. - Preventing data breaches:
Encrypted data is much harder to access and decipher, reducing the likelihood of successful data breaches. - Complying with data protection regulations:
Data protection regulations require organizations to secure sensitive data, making encryption a crucial tool for compliance. - Building trust with customers:
Customers expect their data to be secure, and encryption is a key way to demonstrate that an organization takes data security seriously. - Securing communication:
Encrypted communication channels help to ensure that data transmitted over legacy systems cannot be intercepted or tampered with. - Preventing intellectual property theft:
Encryption can help to protect sensitive intellectual property, such as trade secrets or proprietary information.
Overall, encryption is critical for protecting sensitive information, and ensuring data privacy and security. In addition, it is important for individuals and organizations to implement encryption measures in order to protect their information and comply with data protection regulations. If you’re new to encryption, we recommend visiting our Beginner’s Guide to Encryption white paper.
Outdated Databases Need Encryption
Legacy databases, particularly those running on unsupported versions of SQL Server, may lack the latest security features and updates. This can leave them vulnerable to data breaches and other security threats. Upgrading to the latest version of SQL Server may provide access to improved security features, as well as better support and maintenance from Microsoft.
However, the time and expense of upgrading your SQL Server can be burdensome. Upgrades often involve new equipment, code changes and significant time for testing and migration. If upgrading is not feasible, it is still important to implement encryption to protect sensitive data stored in legacy databases. Encryption can help prevent unauthorized access and protect against data breaches. Resources and tools are often available to support older legacy systems.
Overall, legacy databases need to be secured with encryption, regardless of whether upgrading to the latest version of software is an option or not. By doing so, companies can ensure that sensitive information stored in these databases remains protected from security threats.
The Risks of NOT Securing Your Legacy Systems
Legacy systems, which are outdated and often no longer supported by their vendors, may contain security vulnerabilities that can expose your systems and data to attacks. The risks of not securing these systems can be significant and include:
- Security vulnerabilities:
Legacy systems may contain security vulnerabilities that could be exploited by hackers to steal sensitive information, install malware, or launch other types of attacks. - Compliance issues:
Many industries have strict regulatory requirements for data security and privacy. Failure to secure your legacy systems can lead to non-compliance with these regulations, which can result in fines, lawsuits, and other legal consequences. - Data breaches:
Legacy systems that are not properly secured can be vulnerable to data breaches, resulting in the theft of sensitive data, such as personal information, financial data, and intellectual property. This can damage your reputation and lead to legal liabilities. - Business disruption:
A security breach or data loss can disrupt your business operations, leading to downtime, lost revenue, and damage to your brand. - Cost of remediation:
A security breach or data loss can incur significant cost for remediation, including the cost of investigating the breach, repairing the damage, compensating affected customers, and paying fines.
To mitigate these risks, it is important to take steps to secure your legacy systems. By doing so, you can protect your business from potential security threats and maintain compliance with data protection regulations.
What is a cost-effective way for organizations to secure the data on their legacy systems and achieve compliance with modern laws?

Our Encryption Solution for Legacy Databases
Our SQL Server Encryption Solution supports transparent data encryption for all versions from SQL Server 2000 and later. The Encryptionizer solution deploys quickly and easily with point-and-click GUIs with no additional programming, maintenance, or ongoing administration required. Protect all of your intellectual property while making them seamlessly accessible through your application or website including SQL databases, system database, backups, FileStream, and unstructured files.
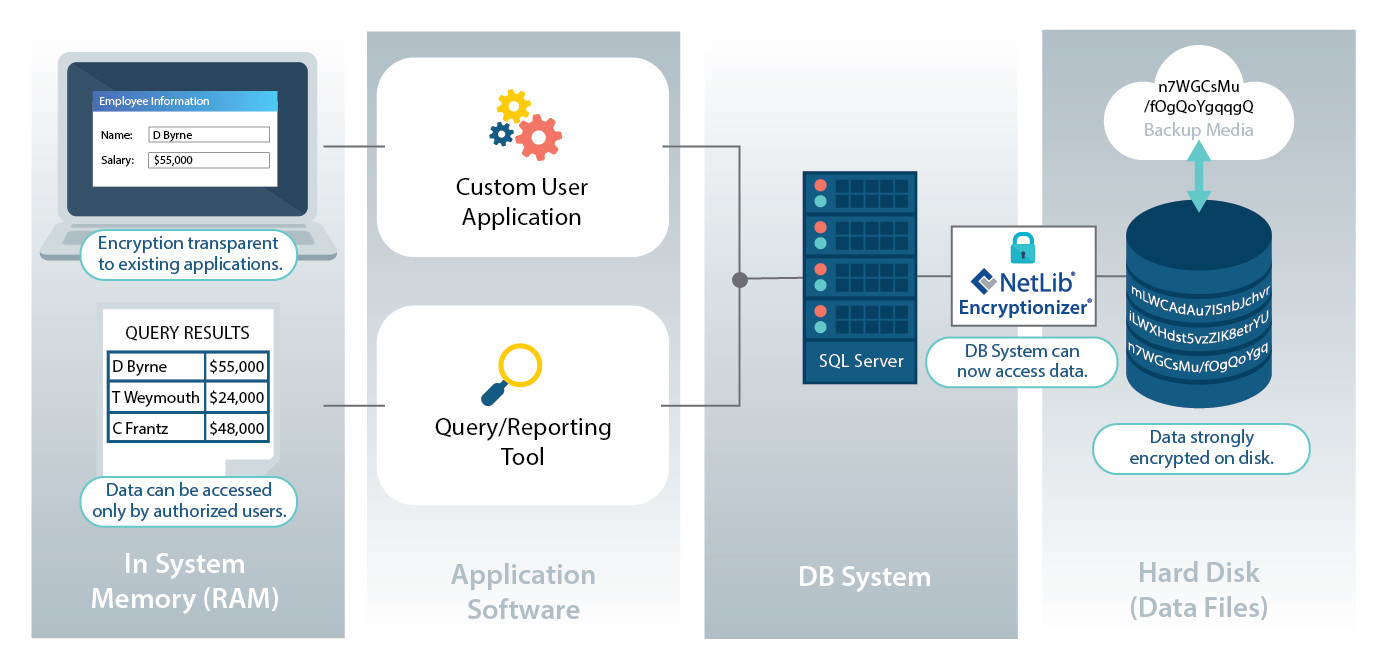
To learn more about how Encryptionizer’s Transparent Encryption works click here.
About NetLib Security
NetLib Security has spent the past 20+ years developing a powerful, patented solution that starts by setting up a formidable offense for every environment where your data resides: physical, virtual and cloud. Our platform simplifies the process while ensuring high levels of security.
Simplify your data security needs. Encryptionizer is easy to deploy. It is a cost-effective way to proactively and transparently protect your sensitive data that allows you to quickly and confidently meet your security requirements. With budget considerations in mind, we have designed an affordable data security platform that protects, manages, and defends your data, while responding to the ever changing compliance requirements.
Data breaches are expensive. Security does not have to be.
NetLib Security works with government agencies, healthcare organizations, small to large enterprises, financial services, credit card processors, distributors, and resellers to provide a flexible data security solution that meets their evolving needs. To learn more or request a free evaluation visit us at www.netlibsecurity.com.
