Data at Rest vs Data in Transit
The importance of data protection cannot be overstated, especially with the exponential growth of data creation and storage in recent years. It has become imperative for organizations to ensure the safety of their confidential information to operate effectively. However, protection needs vary depending on the nature of the data. Some may need to protect the information stored on their mobile devices or laptops in case of loss or theft, while others may need to secure their documentation on file servers. In some cases, data needs protection during transmission via email or when stored in the cloud. To develop an effective Data Protection Strategy, it’s crucial to identify all types of information that require protection and implement appropriate safeguards.
What is Data at Rest?
Data at rest refers to information that is stored or archived, and is not moving between devices or networks. While this type of data is typically less vulnerable than transmitted data, it is often considered more valuable to hackers. Stored data usually contains a complete set of sensitive information, rather than the bits and pieces that might be transmitted over networks. Examples of data at rest include file servers & network shares, Document Management Systems (DMS), external storage, Database Management Systems (DBMS), endpoints, laptops, PCs, mobile devices, and cloud storage.
To ensure that data is secure at rest, it must be encrypted. Encryption requires a hacker to spend an impossibly long amount of time in a brute-force attack that uses trial-and-error to guess login information, encryption keys, or backdoors in order to decrypt the data. It is important to ensure that the encryption keys are not stored with the data, that the keys are of sufficient length and do not use any plain language words. By encrypting data at rest, organizations can significantly reduce the risk of unauthorized access and maintain the confidentiality of their sensitive information.
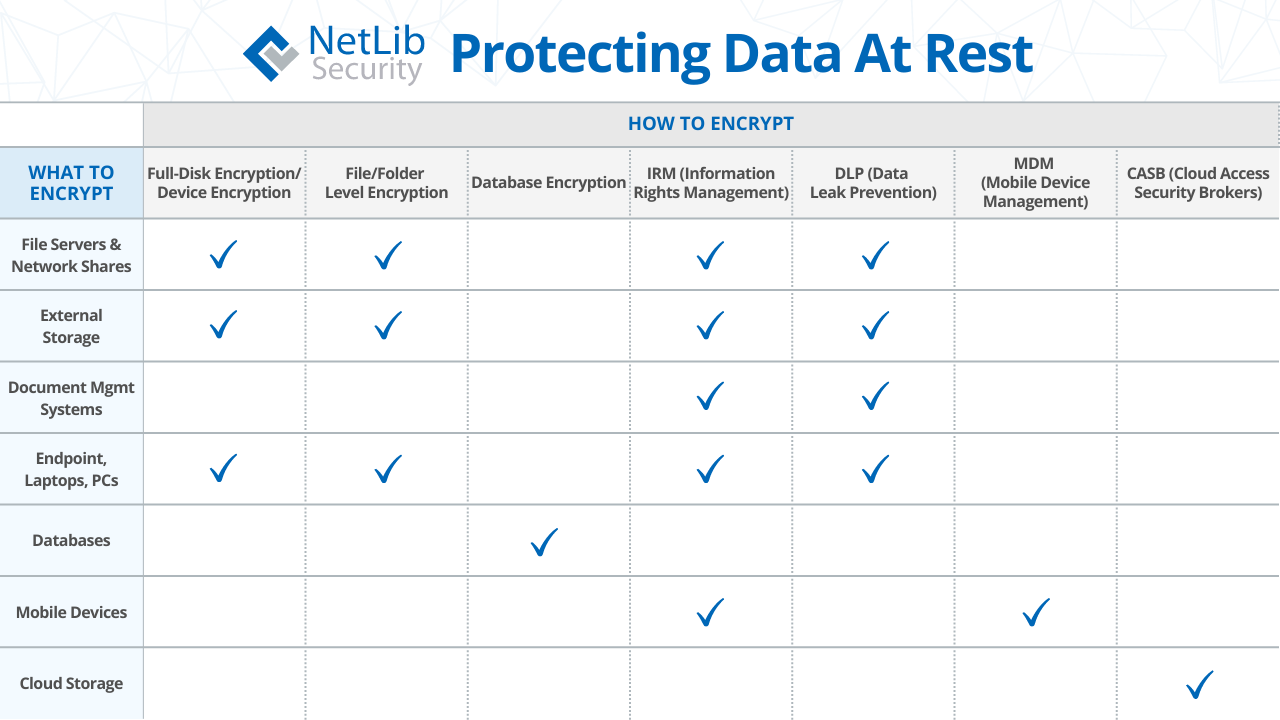
To protect data at rest, organizations can use security software, firewalls, and encryption. While firewalls and other perimeter defenses work to protect against invasion, those measures are insufficient when the intruder gets through. Encryption makes the data unreadable to hackers in the event that the perimeter is breached. NetLib Security’s Encryptionizer is a high-performance data security platform that offers top-level protection for your sensitive information. It encrypts your data seamlessly across physical, virtual, and cloud environments, with virtually no impact on performance, ensuring business continuity.
While encrypting an entire database is a smart solution, organizations can also opt to add another layer of security with column encryption to further protect select data within the broader dataset. It is important to understand the differences between whole database and column level encryption to make an informed decision that aligns with the organization’s goals. By implementing proper encryption techniques, organizations can ensure that their data at rest is secured and not accessible to unauthorized parties.
What is Data in Transit?
Data in transit, also known as data in motion, refers to the information that is in the process of moving from one location to another, such as emails, downloads, uploads, LAN transfers, cloud transfers, and collaboration tools. This type of data includes any information that is transmitted over the internet or a corporate network, and is more vulnerable to cyber attacks than data at rest. Data and files traveling through Microsoft Teams, Slack, WhatsApp or any other communications channel are also examples of data in transit.
To protect data in transit, companies should implement network security controls such as firewalls and network access controls. It is also essential to identify critical assets and their vulnerabilities and implement automated controls in addition to firewalls. Email encryption has become a mandatory practice to secure communication channels from potential threats. Companies can utilize data loss prevention (DLP) solutions to scan emails and attachments for anything suspicious and evaluate potential risks.
Encryption in transit can be achieved using network or application-level protocols that perform encryption. For example, a VPN connection that uses secure protocols to encrypt traffic is a common method for encryption in transit. Websites and endpoints that are accessible only via the HTTPS protocol guarantee their data is encrypted with SSL. By implementing these practices, organizations can ensure that their data in transit is protected from unauthorized access and cyber threats.
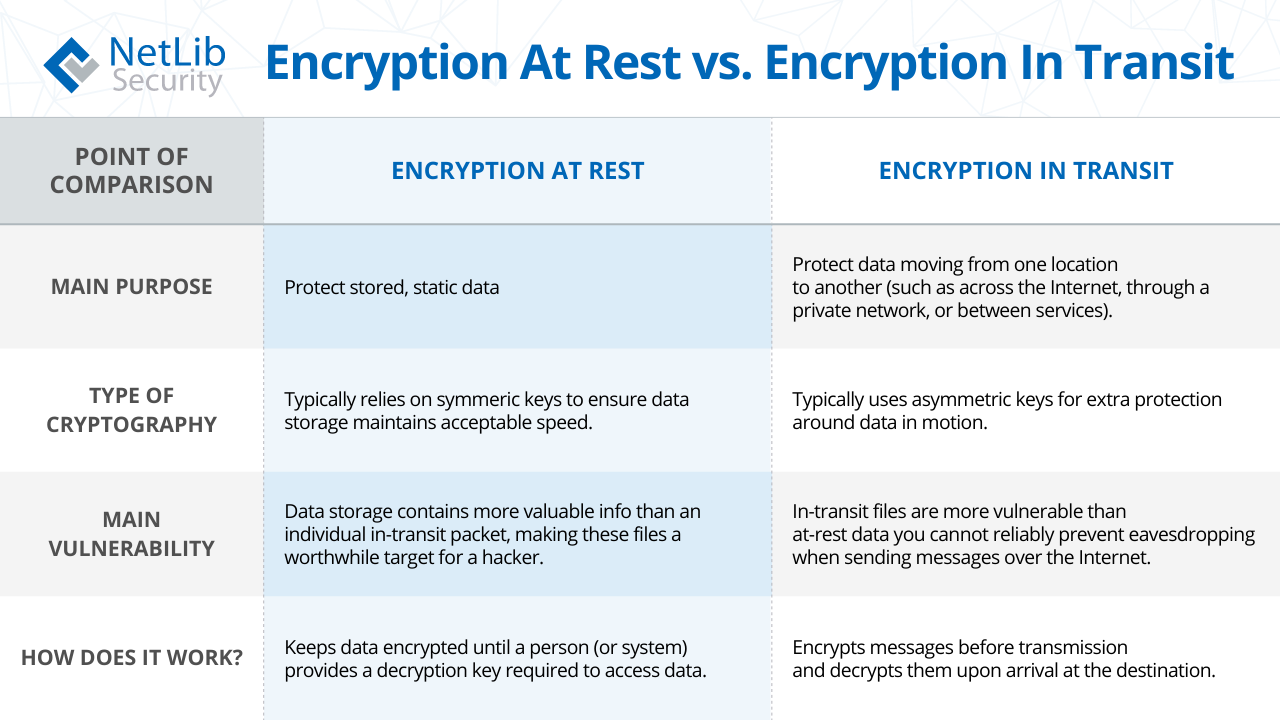
Comparing Encryption of Data at Rest vs Data in Transit
See our chart below on understanding the difference between protecting data at rest versus data in transit using encryption.
About NetLib Security
NetLib Security has spent the past 20+ years developing a powerful, patented solution that starts by setting up a formidable offense for every environment where your data resides: physical, virtual and cloud. Our platform simplifies the process while ensuring high levels of security.
Simplify your data security needs. Encryptionizer is easy to deploy. It is a cost-effective way to proactively and transparently protect your sensitive data that allows you to quickly and confidently meet your security requirements. With budget considerations in mind, we have designed an affordable data security platform that protects, manages, and defends your data, while responding to the ever changing compliance requirements.
Data breaches are expensive. Security does not have to be.
NetLib Security works with government agencies, healthcare organizations, small to large enterprises, financial services, credit card processors, distributors, and resellers to provide a flexible data security solution that meets their evolving needs. To learn more or request a free evaluation visit us at www.netlibsecurity.com.
——————-
March 16, 2023
Originally published at: https://www.netlibsecurity.com
Copyright: NetLib Security, Inc.
