The Right Encryption Software For Developers and DBAs
The need to protect personally identifiable information (PII), protected health data (PHI), and payment card industry data (PCI) has become more critical as hacking incidents continue to become more frequent and costly. Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching over $10 trillion annually.
 In spite of an increasingly strict regulatory environment, data breaches have continued unabated. Faced with the requirement to comply with international standards, organizations need to protect sensitive data in both local and cloud environments. Database encryption is an essential component of any plan to enhance digital security and privacy. If you don’t already have an approach in place to protect your organization from potential hackers, we recommend you read our Defensive Strategy for Database Encryption article.
In spite of an increasingly strict regulatory environment, data breaches have continued unabated. Faced with the requirement to comply with international standards, organizations need to protect sensitive data in both local and cloud environments. Database encryption is an essential component of any plan to enhance digital security and privacy. If you don’t already have an approach in place to protect your organization from potential hackers, we recommend you read our Defensive Strategy for Database Encryption article.
With so many applications and services available for database encryption, it can be difficult to know which one is right for you. In this article, we’ve compiled information to help you understand what to look for and which software best fits your needs.
Understanding the Purpose of Encryption Software
Encryption refers to the means of securing information so it can’t be read by third parties. Specifically, encryption runs your data through a complex algorithm on both sides of a transaction: storage and retrieval. Encryption keeps individual files, or an entire file system, safe on a device. It protects data in the case of theft and unauthorized access by ensuring the data is unusable to any application that is not authorized to decipher it. Encryption software uses a string of alphanumeric characters, plus an algorithm that operates as a key to lock and unlock data. When you encrypt a file with a unique key, the information is scrambled by a mathematical formula which ensures that the information cannot be read again until it has been decrypted by an authorized application.
Know What You Are Looking For
With so many options available, it’s helpful to understand how different types of encryption software operate. Encryption can be applied at one of four layers: Application, Database, File System, and Device Storage.
 The lower in the stack encryption is employed, the simpler and less intrusive the implementation will be. Low level encryption, however, addresses a smaller number of threats. By employing encryption higher in the stack, organizations can typically realize improved security and mitigate more threats.
The lower in the stack encryption is employed, the simpler and less intrusive the implementation will be. Low level encryption, however, addresses a smaller number of threats. By employing encryption higher in the stack, organizations can typically realize improved security and mitigate more threats.
Do Your Research
When looking for Encryption software, it’s important to compare vendors’ feature lists using unbiased and objective criteria. Be suspicious of free products that might cost a lot more than you think when you include complex long implementation times, technical support and user training. Here are some questions to keep in mind as you search for a data encryption solution.
- Does The Solution Match Your Threats?
To determine your answer to this question, do a quick risk analysis – ask yourself what threats are you trying to address? Your encryption solution should solve your actual needs.
- At What Layer(s) Do You Want To Encrypt Data?
There are a variety of ways that you can encrypt data. In the previous section, we mentioned a few layers. It is important that you understand which layer you will need protection for.
- How Much User Training And Technical Support Will Be Required? Is there a Free Trial?
People often resist change, especially if it means adding significant time to their already busy day. Understanding the training required for the encryption solution you select is important. Free trials provide you with hands-on experience that can help you determine if the encryption solution fits your organization and is right for you. A trial period will allow you to truly understand how the solution works in your own environment without the initial long-term commitment.
- Is The Product Compatible With Your Applications And Infrastructure?
The encryption solution you select should be compatible with your existing operating systems, software and applications. A solution that requires updates, upgrades or replacements can be expensive and time consuming, even before you implement your new encryption solution. Instead, try to leverage your previous investments.
- What Operating Systems And Platforms Are Supported?
Your operating system and platform does not always support all types of encryption, so when selecting the best encryption solution you must be sure that the encryption software works with your primary platforms.
- Can The Product Encrypt Personal Devices – Backups, Portable Drives, Etc.?
Sensitive data doesn’t exist only on computers, but also on phones, tablets, USB drives, backup tapes, etc. In selecting your encryption solution, ensure that you consider these files and how to ensure that users only save sensitive data on encrypted drives.
- Can You Recover Encrypted Data When Keys Are Lost?
Determine if your encryption solution has a reliable recovery method. It should be scalable to your organization. And the recovery method itself should be secure.
- How Are Keys Created, Stored, Changed and Archived?
Vulnerabilities can be introduced by poor key management policies. Understanding how keys are created, stored, and changed is important to the decision making process.
- What Is the Impact if the Product Fails?
Understand what happens when the product fails. Would your data now be at risk? How would you create a response plan if it does?
- What About The Future – Will You Be Vendor-Locked Forever?
Thinking ahead, you want to be sure you understand what options you have with the encryption solution. Can you upgrade it if necessary? Are you locked in?
Benefits of Encryption Software for Developers and DBA’s
Database Administrators have been charged with the responsibility to manage and safeguard the stored data for their corporations. This can include data stored in legacy systems, backups and new installations.
Developers of distributed applications have two challenges: existing applications and new development. Applications already in the field might have vulnerable data exposed, whether they be distributed across their corporate environment or their customer locations. The new work-from-home policies have added even more complications. With new development, Developers should also be creating new applications with security in mind from the start.
Encryption software makes meeting regulatory compliance and operationalizing data security models easier. And the benefits of encryption software for developers include confidentiality, compliance, and reduced legal risk.
Your encryption solution should be simple and comprehensive, without requiring you to become an expert in encryption and security yourself.
Does NetLib Security’s Encryptionizer Software work for you?
Below we review the questions asked above against our product, NetLib Encryptionizer, to help see if we’re a good fit for your business or project. Our software has been implemented to satisfy security needs in many segments including businesses, developers, healthcare, financial, government, and education.
- Does The Solution Match Your Threats?
Virtually every new privacy and data protection regulation has required an encryption component. Encryptionizer provides a simple solution to encrypt stored data easily and transparently with no impact on your end users, and low total cost of ownership.
- At What Layer(s) Do You Want To Encrypt Data?
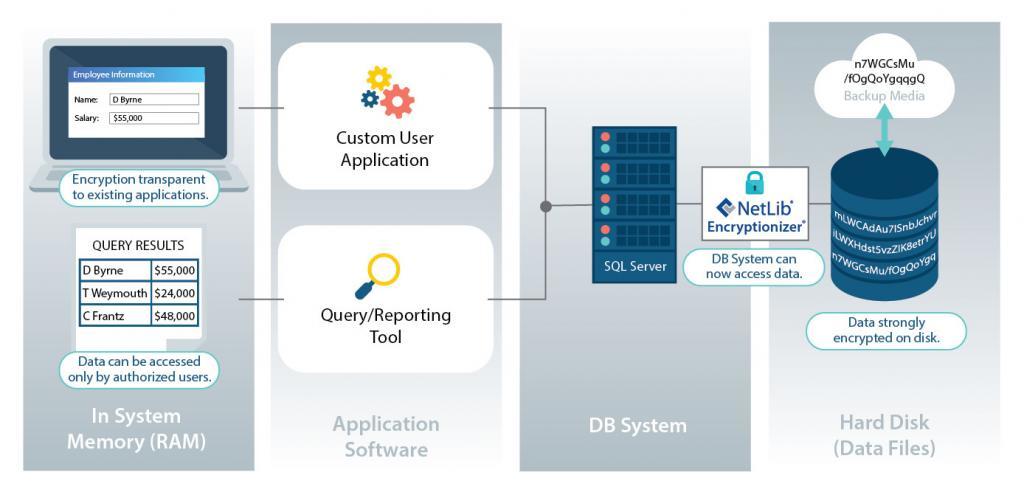
Encryptionizer protects data at the Database and Application Level. Typically Volume or Disk level encryption is controlled by the computer owner or administrator. Database and Application level encryption puts the control in the hands of the data owner.
- How Much User Training And Technical Support Will Be Required?
NetLib Security’s Encryptionizer is built with intuitive interfaces which guide you through the process. It does not require training, and you can typically implement it in less than an hour. And there should be no impact whatsoever on end-users. It is important, however, to understand how the software works which is why we offer a Free Evaluation of our product, along with detailed documentation. We want our customers to see how easy the product is to use, and to make sure we are the right solution for them in their own environment.
- Is The Product Compatible With Your Applications And Infrastructure?
Encryptionizer is built with the ability to work transparently to Applications. The user of the protected application does not need to know encryption keys or passwords beyond any security you already have set up in your app. It does not require any changes to your existing infrastructure. No new hardware needed. No upgrades to existing systems required.
- What Operating Systems And Platforms Are Supported?
Encryptionizer is transparent to any application or databases on the Windows platform – device, desktop, server or cloud. It works on every operating system from Windows Server 2008-R2 through 2022, Win 7 through Win 11. NetLib Security has a version specifically tuned to SQL Server, supporting every version and edition from 2005 through 2021, from Enterprise down to SQL Express and LocalDB. Encryptionizer can also protect other database management systems such as MySQL, PostgreSQL, MongoDB and more. Although some encryption solutions focus only on database systems, Encryptionizer also supports protection of website data, and the transparent encryption of data types such as documents, images, and other files.
- Will The Product Encrypt PDAs, Backups, Portable Drives, Etc.?
Encryptionizer allows you to encrypt data wherever your application stores it – whether locally, on portable/removable media, or in a network location.
- Can You Recover Encrypted Data When Keys Are Lost?
Encryptionizer provides a key recovery mechanism should a key be lost. For even greater security and protection of keys, NetLib Security offers the Encryptionizer Key Manager product where keys can be stored on a central key server, backed up, and rotated.
- How Are Keys Created, Stored, Changed and Archived?
By default, encryption keys are stored in strongly encrypted files outside of the protected data. They can be stored locally or to a protected network location. Data owners have the ability to change keys at any time as business policy dictates. The Encryptionizer Key Manager provides the additional function of centralized key management, storage and archival which can be used and shared with multiple systems.
- What Is the Impact if the Product Fails?
Encryptionizer is a stable and mature product. As a FIPS 140-2 validated solution, Encryptionizer performs numerous self-tests to ensure that no software tampering has occurred. If Encryptionizer fails to start, the keys are simply not passed to the application working with the encrypted data. The data itself remains intact, safe and protected, just not accessible until issues are resolved. NetLib Security has knowledgeable support staff which works directly with the customer to resolve any issues.
- What About The Future – Will You Be Vendor-Locked Forever?
Encryptionizer cryptography is proprietary and unique. No other encryption product can be used to access the encrypted data. This is an important anti-hacking feature that prevents others from utilizing common techniques to read the encrypted data. Anything encrypted with Encryptionizer can only be read by applications secured with Encryptionizer. However, if a user decides to later change security methods, data can be decrypted, and systems will return to their original state.
We hope that these questions will aid you in your decision making in choosing your encryption solution. It can be overwhelming to select the right fit for your company but it is critical to protect your data. Take it step by step! Print this article and start asking your vendor some questions and the answers may surprise you. Be aware that finding the perfect fit may take some time.
About NetLib Security
NetLib Security has spent the past 20+ years developing a powerful, patented solution that starts by setting up a formidable offense which can be managed from anywhere in the world, across every environment where your data resides: physical, virtual and cloud. Our platform is geared to simplify the process for you while ensuring unprecedented levels of security are in place.
You can simplify your data security needs by utilizing Encryptionizer to satisfy your security requirements quickly, and with confidence. These days it’s essential to protect the safety, integrity and confidentiality of sensitive data. NetLib Security’s unique encryption solutions are an easy and cost effective way to proactively and transparently protect your data. We also understand budget considerations are a constant concern, which is why we designed an affordable data security platform to protect, manage and defend while enabling the growing areas of compliance. Protecting your data doesn’t have to break the bank, but not protecting it will.
NetLib Security works closely with government agencies, healthcare organizations, small to large enterprises spanning financial services, credit card processors, distributors, and resellers to deliver a flexible data security solution to meet their ever changing needs. For more information or to request a free evaluation visit us at www.netlibsecurity.com.
——————-
Sept 6, 2022
Originally published at: https://www.netlibsecurity.com
Copyright: NetLib Security, Inc.
