Protect Your Business from Malicious Hackers
An astounding 64% of companies worldwide have experienced at least one form of cyber attack. And because the pandemic accelerated the shift to telecommuting, many corporations have not had a chance to update their security protocols to deal with the risks inherent in remote work. This has created a tempting target for malicious actors who seek to exploit companies’ technological weaknesses. The Washington Post states that “if the past is a prologue, 2022 is likely to be a year of big hacks, big threats and plenty more crises.”
Protection is Key
Substandard security practices such as simple passwords or single factor authentication cause organizations to become attractive soft targets and contribute to successful cyberattacks. Those attacks can be prevented or mitigated by fully implementing more stringent security requirements.
We’ve created a compilation of Data Security Best Practices For Businesses in 2022 to help you simplify security and protect stored data while meeting compliance requirements. If a hacker is able to get inside the organization, they are able to access different accounts, move to multiple computer systems, deploy malicious software and obtain sensitive data. Having a plan in place will help organizations quickly shut down systems to mitigate the damage.
Critical for Every Industry
Organizations should be proactive in addressing their cyber risks by planning for worst-case scenarios, developing security systems to prevent attacks, and limiting the consequential damage when attacks occur. While many organizations understand the importance of data security, many do not have the experience to develop a solution that meets their unique needs.
Below we describe cases we’ve encountered with our own customers.
Finance
MIMICS, a financial software firm, focuses its resources on protecting client data by encrypting databases, managing access, and safeguarding intellectual property. When handling sensitive data for themselves as well as their clients, it is imperative that they take steps to secure its databases. Beyond encrypting the stored data on their databases, priorities include: protecting SQL access levels, preventing data manipulation, limiting database access to a select few, and safeguarding MIMICS intellectual property. NetLib Security and MIMICS continue efforts to ensure they secure sensitive customer data and achieve compliance with data protection standards.
Healthcare
A Medical Device Manufacturer (MDM) made protecting their patient data and complying with all pertinent privacy regulations a top priority. Meeting these requirements was a major goal for this MDM with thousands of employees and customers worldwide. The continually updated FDA guidelines, in addition to the requirements of the HIPAA-HiTech law, created even more rules and regulations for the nearly century-old company to follow. Personal health information (PHI) is a critical component of healthcare operations, as well as a valuable target for hackers. Complying with these regulations is a complex task. After more than a year and half of searching, the firm was still unable to find a solution that met its needs. That all changed when they found NetLib Security. The MDM had been looking for a product that could be included in their diverse suite of servers and medical devices, using a standardized answer rather than a patchwork set of solutions. For the past several years, NetLib Security has been working with this MDM’s team to help meet key business objectives of securing sensitive health data stored on their devices.
Small Businesses
Regulations have been driving corporations to implement data security solutions. Compliance with these new standards was the goal for LiftFund, a nonprofit approaching three decades of business, with a focus on microlending to small companies. Since its inception, the company has made more than 23,000 loans for a total of over $372 million. With a varied client base, including small businesses, startups, and partnerships with financial institutions, the requirements for compliance were pressing. What LiftFund needed was a solution that could help mitigate the risk of their customers’ data being compromised, as well as protect their own Personally Identifiable Information (PII) from malicious actors or accidents. Encrypting their databases, folders and web server data was of paramount importance, as they sought compliance with SOC 2 (Service Organization Control 2) and GLBA (Gramm-Leach-Bliley Act). Ease of deployment, cost efficiency, and securing their application data on site were further factors in their decision.
How Encryption Can Help
Encryption is a basic building block of data security, allowing systems to conceal information by altering it to look like random meaningless data. If you’re interested in learning more about encryption, check out our Beginner’s Guide to Encryption for Compliance and Data Protection.
Your customers expect you to protect their data. As a responsible corporation, you must do what you need to maintain your customers’ trust. If an organization were to be attacked, encryption adds a layer of protection, making the data useless if it is stolen. Any information that sits in your database, data-at rest, represents the largest target for theft due to the sheer volume of information organizations typically store in their databases. Database encryption makes information unreadable unless accessed by authorized users with the correct key.
NetLib Security’s solutions offer transparent encryption of stored data, providing a critical component of any company’s data security protocol. . In the fight against cyber criminals, every measure must be taken to provide powerful protection for sensitive data. Keeping data encrypted ensures a substantial mitigation of damage for when an intruder gets through.
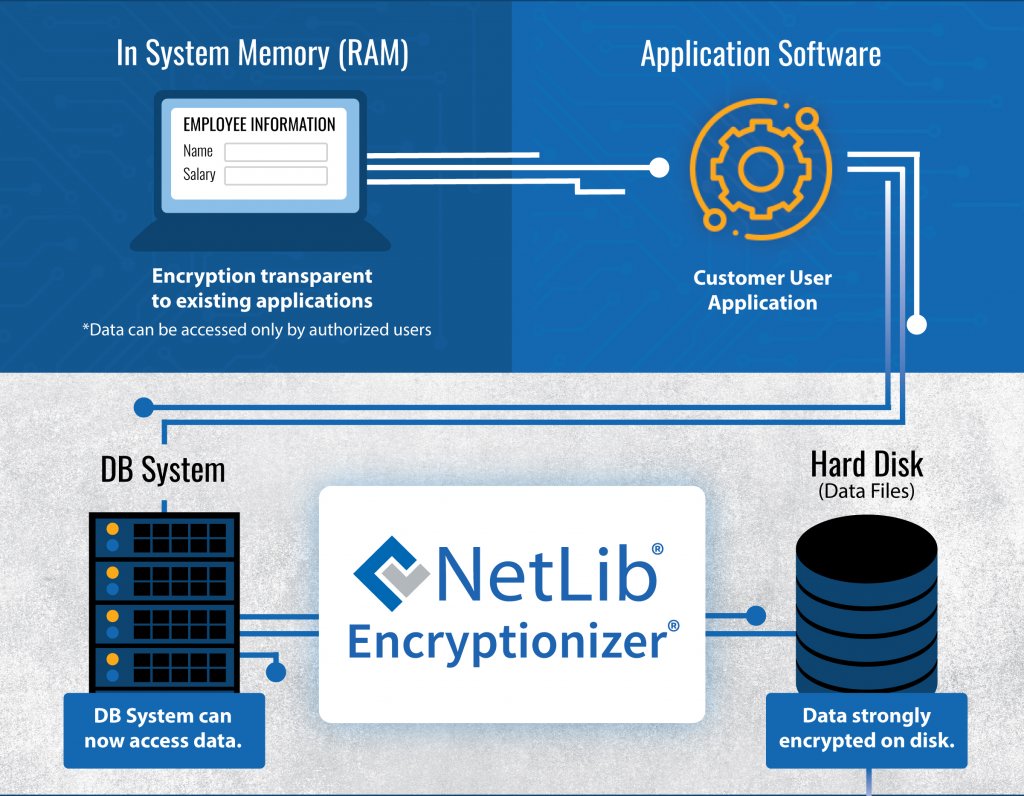 NetLib Security’s patented, high performance data security platform, Encryptionizer, simplifies security for your stored data right out of the box. Your data is encrypted and secure even if someone gets in. In a few clicks, it transparently encrypts your stored data on systems, devices and distributed applications with virtually no impact on performance, and no programming required.
NetLib Security’s patented, high performance data security platform, Encryptionizer, simplifies security for your stored data right out of the box. Your data is encrypted and secure even if someone gets in. In a few clicks, it transparently encrypts your stored data on systems, devices and distributed applications with virtually no impact on performance, and no programming required.
If you’re interested in NetLib Security’s Encryptionizer, request a FREE 30-day evaluation of our product. Easily deployed in a few steps to satisfy a pressing need quickly, and with confidence.
Not sure if encryption would be right for you? See our Beginner’s Guide to Encryption for Compliance and Data Protection for a more detailed explanation on how it works.
About NetLib Security
NetLib Security has spent the past 20+ years developing a powerful, patented solution that starts by setting up a formidable offense which can be managed from anywhere in the world, across every environment where your data resides: physical, virtual and cloud. Our platform is geared to simplify the process for you while ensuring unprecedented levels of security are in place.
You can simplify your data security needs by utilizing Encryptionizer to satisfy your security requirements quickly, and with confidence. These days it’s essential to protect the safety, integrity and confidentiality of sensitive data. NetLib Security’s unique encryption solutions are an easy and cost effective way to proactively and transparently protect your data.
We also understand budget considerations are a constant concern, which is why we designed an affordable data security platform to protect, manage and defend while enabling the growing areas of compliance. Protecting your data doesn’t have to break the bank, but not protecting it will.
NetLib Security works closely with government agencies, healthcare organizations, small to large enterprises spanning financial services, credit card processors, distributors, and resellers to deliver a flexible data security solution to meet their ever changing needs.
——————-
Jun 2, 2022
Originally published at: https://www.netlibsecurity.com
Copyright: NetLib Security, Inc.
